*************************************
Update on 10/27/2013. View also
*************************************
Neutron basic RDO setup (havana 2013.2) to have original LAN as external on Fedora 19 with native Ethernet interfaces names
http://bderzhavets.blogspot.ru/2013/10/neutron-basic-rdo-setup-havana-20132-to_26.html
************************************Follow as normal http://openstack.redhat.com/Quickstart, just after
$ sudo yum install -y openstack-packstack run $ sudo yum -y update one more time to upgrade python-backports to 1.0.4
Post install fix (as of 10/31/2013) :
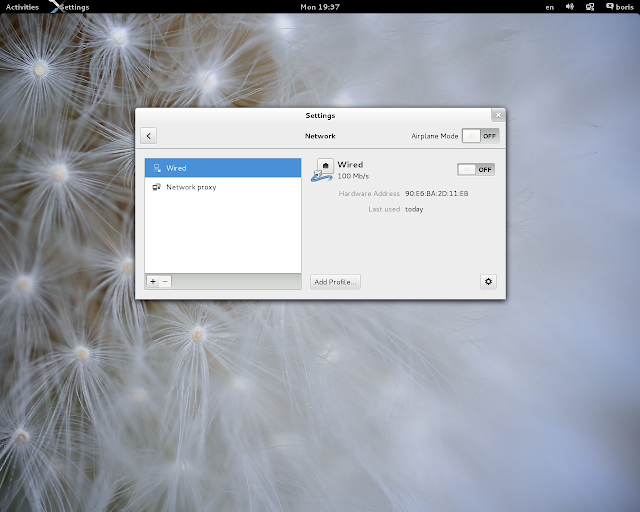
Also set ALLOWED_HOSTS = ['*'] in /etc/openstack-dashboard/local_settings and restart httpdWhen done switch to eth0 per
http://unix.stackexchange.com/questions/81834/how-can-i-change-the-default-ens33-network-device-to-old-eth0-on-fedora-19
Remove biosdevname if it is installed. (yum remove biosdevname)
Disable the udev rule:
ln -s /dev/null /etc/udev/rules.d/80-net-name-slot.rules
Reboot
and create under /etc/sysconfig/network-scripts
[root@localhost network-scripts]# cat ifcfg-br-ex
DEVICE="br-ex"
BOOTPROTO="static"
IPADDR="192.168.1.125"
NETMASK="255.255.255.0"
DNS1="83.221.202.254"
BROADCAST="192.168.1.255"
GATEWAY="192.168.1.1"
NM_CONTROLLED="no"
DEFROUTE="yes"
IPV4_FAILURE_FATAL="yes"
IPV6INIT=no
ONBOOT="yes"
TYPE="OVSBridge"
DEVICETYPE="ovs"
[root@localhost network-scripts]# cat ifcfg-eth0
NAME="eth0"
HWADDR=90:E6:BA:2D:11:EB
ONBOOT="yes"
TYPE="OVSPort"
DEVICETYPE="ovs"
OVS_BRIDGE=br-ex
NM_CONTROLLED=no
IPV6INIT=no
Enable network service, turn off interface eth0
********************************
UPDATE on 12/17/2013
********************************
It's working again
5e1fc460-3882-4210-b185-310e00af8a47
Bridge br-int
Port br-int
Interface br-int
type: internal
Port "tapf7dd77e3-50"
tag: 1
Interface "tapf7dd77e3-50"
type: internal
Port "qr-33f43f85-da"
tag: 1
Interface "qr-33f43f85-da"
type: internal
Bridge br-ex
Port "qg-161a8f7c-01"
Interface "qg-161a8f7c-01"
type: internal
Port br-ex
Interface br-ex
type: internal
Port "eth0\nbr-ex"
Interface "eth0\nbr-ex"
Port "eth0"
Interface "eth0"
ovs_version: "1.11.0"
**************************************************************************
Due to known bugs
Bug 981583 - Openstack firewall rules are not enabled after reboot
https://bugzilla.redhat.com/show_bug.cgi?id=981583
Bug 981652 - firewalld does not cover openstack/packstack use case.
https://bugzilla.redhat.com/show_bug.cgi?id=981652
Run:-
# yum -y install iptables-services
# systemctl disable firewalld
# systemctl enable iptables
then reboot
In dashboard environment delete router1 and public network.
# source keystonerc_admin
# nova secgroup-add-rule default icmp -1 -1 0.0.0.0/0
# nova secgroup-add-rule default tcp 22 22 0.0.0.0/0
# neutron net-create public --router:external=True
# neutron subnet-create public 192.168.1.0/24 --name vlan --enable_dhcp False \
--allocation_pool start=192.168.1.57,end=192.168.1.92 \
--gateway 192.168.1.1
# neutron floatingip-create public
# EXTERNAL_NETWORK_ID=`neutron net-list | grep public | awk '{ print $2 }'`
# INT_SUBNET_ID=`neutron subnet-list | grep private_subnet | awk '{ print $2}'`
# SERVICE_TENANT_ID=`keystone tenant-list | grep service | awk '{ print $2}'`
# neutron router-create --name router2 --tenant-id $SERVICE_TENANT_ID router2
# neutron router-gateway-set router2 $EXTERNAL_NETWORK_ID
# neutron router-interface-add router2 $INT_SUBNET_ID
# neutron subnet-update $INT_SUBNET_ID --dns_nameservers list=true 83.221.202.254
# neutron subnet-update $INT_SUBNET_ID --gateway_ip 10.0.0.1
Create images via command line :-
# glance image-create --name 'Fedora19image' --disk-format qcow2 --container-format bare --is-public true \
--copy-from http://cloud.fedoraproject.org/fedora-19.x86_64.qcow2
# glance image-create --name 'UbuntuServer13.10image' \
--disk-format qcow2 \
--container-format bare --is-public true \
--copy-from http://cloud-images.ubuntu.com/saucy/current/saucy-server-cloudimg-amd64-disk1.img
You can also fix the issue per
http://openstack.redhat.com/forum/discussion/554/havana-horizon-no-formats-available-for-images
Creating volumes on Havana release
By default (not to follow [1]) cinder-volumes VG gets created under
/var/lib/cinder as loop mounted empty file due to :-
[root@localhost ~(keystone_admin)]# cd /var/lib/cinder
[root@localhost cinder(keystone_admin)]# ls -l
total 16777236
-rw-r--r--. 1 root root 22118662144 Oct 7 16:04 cinder-volumes
drwxr-xr-x. 2 cinder cinder 4096 Oct 7 15:48 tmp
[root@localhost cinder(keystone_admin)]# losetup -a
/dev/loop0: [64768]:6034065 (/srv/loopback-device/device1)
/dev/loop1: [64768]:918092 (/var/lib/cinder/cinder-volumes)
[root@localhost ~(keystone_admin)]# nova image-list
+--------------------------------------+------------------------+--------+--------+
| ID | Name | Status | Server |
+--------------------------------------+------------------------+--------+--------+
| 73ddfddf-833d-4eda-869f-e26321c20a2e | Fedora19image | ACTIVE | |
| 2d5f5596-c5f5-401a-ae16-388b5dae78f2 | UbuntuServer13.10image | ACTIVE
| 0415ec26-d202-4fb7-b6a0-3e7923547e98 | cirros | ACTIVE | |
+--------------------------------------+------------------------+--------+--------+
[root@localhost ~(keystone_admin)]# cinder create --image-id 2d5f5596-c5f5-401a-ae16-388b5dae78f2 --display_name SalamanderVG 7
+---------------------+--------------------------------------+
| Property | Value |
+---------------------+--------------------------------------+
| attachments | [] |
| availability_zone | nova |
| bootable | False |
| created_at | 2013-10-07T11:39:32.001108 |
| display_description | None |
| display_name | SlamanderVG |
| id | 624f7b78-bb1e-411a-afc6-e3190187af38 |
| image_id | 2d5f5596-c5f5-401a-ae16-388b5dae78f2 |
| metadata | {} |
| size | 7 |
| snapshot_id | None |
| source_volid | None |
| status | creating |
| volume_type | None |
+---------------------+--------------------------------------+
[root@localhost ~(keystone_admin)]# nova volume-list
+--------------------------------------+-------------+--------------+------+-------------+-------------+
| ID | Status | Display Name | Size | Volume Type | Attached to |
+--------------------------------------+-------------+--------------+------+-------------+-------------+
| 624f7b78-bb1e-411a-afc6-e3190187af38 | downloading | SalamanderVG | 7 | None | |
+--------------------------------------+-------------+--------------+------+-------------+-------------+
[root@localhost ~(keystone_admin)]# cinder create --image-id 73ddfddf-833d-4eda-869f-e26321c20a2e --display_name Fedora19VG 7
+---------------------+--------------------------------------+
| Property | Value |
+---------------------+--------------------------------------+
| attachments | [] |
| availability_zone | nova |
| bootable | False |
| created_at | 2013-10-07T11:42:32.708633 |
| display_description | None |
| display_name | Fedora19VG |
| id | d2745ee6-9166-4ace-9fb6-826999eddcd0 |
| image_id | 73ddfddf-833d-4eda-869f-e26321c20a2e |
| metadata | {} |
| size | 7 |
| snapshot_id | None |
| source_volid | None |
| status | creating |
| volume_type | None |
+---------------------+--------------------------------------+
[root@localhost ~(keystone_admin)]# nova volume-list
+--------------------------------------+-------------+--------------+------+-------------+-------------+
| ID | Status | Display Name | Size | Volume Type | Attached to |
+--------------------------------------+-------------+--------------+------+-------------+-------------+
| d2745ee6-9166-4ace-9fb6-826999eddcd0 | downloading | Fedora19VG | 7 | None | |
| 624f7b78-bb1e-411a-afc6-e3190187af38 | available | SalamanderVG | 7 | None | |
+--------------------------------------+-------------+--------------+------+-------------+-------------+
[root@localhost ~(keystone_admin)]# nova volume-list
+--------------------------------------+--------+--------------+------+-------------+--------------------------------------+
| ID | Status | Display Name | Size | Volume Type | Attached to |
+--------------------------------------+--------+--------------+------+-------------+--------------------------------------+
| d2745ee6-9166-4ace-9fb6-826999eddcd0 | in-use | Fedora19VG | 7 | None | 5dc6569f-42d8-49fb-a3d5-7f3089249952 |
| 624f7b78-bb1e-411a-afc6-e3190187af38 | in-use | SalamanderVG | 7 | None | 3e0a32b4-1045-4d30-9921-b1c2c5140639 |
+--------------------------------------+--------+--------------+------+-------------+--------------------------------------+
[root@localhost ~(keystone_admin)]# pvscan | grep cinder-volumes
PV /dev/loop1 VG cinder-volumes lvm2 [20.60 GiB / 6.60 GiB free]
Status of RDO Havana 6 services
Cloud instance of Ubuntu 13.10 Server running Gnome 3.8.4 installed via PPA ppa:gnome3-team/gnome3 :
- $ sudo add-apt-repository ppa:gnome3-team/gnome3
- $ sudo apt-get update
- $sudo apt-get install gnome-shell ubuntu-gnome-desktop
View
http://www.techrepublic.com/blog/linux-and-open-source/how-to-install-gnome-38-on-ubuntu/
regarding setup Gnome 3.8 on Ubuntu 13.04 (10)
REFERENCES
1. http://funwithlinux.net/2013/08/install-openstack-grizzly-on-fedora-19-using-packstack-with-quantum-networking/
2. http://www.blog.sandro-mathys.ch/2013/08/install-rdo-havana-2-on-fedora-19-and.html