Sshuttle may be installed on Fedora 24 via straight forward `dnf -y install sshuttle` [Fedora 24 Update: sshuttle-0.78.0-2.fc24]. Set up F24 as WKS for "TripleO instack-virt-setup overcloud/undercloud deployment
to VIRTHOST" via
ssh (trusted) connection . This setup works much more stable then configuring
FoxyProxy on VIRTHOST running "instack" ( actually undercloud VM) hosting
heat stack "overcloud" and several overcloud Controllers and Compute VMs
Instack-virt-setup deployments don't provide ( vs QuickStart ) ksmd daemon
sharing pages between overcloud VMs ( and supporting copy-on-write feature)
what results significantly more memory utilization on VIRTHOST and require
better CPUs and 48 GB RAM for testing HA overcloud deployments.
Regarding KSM see https://en.wikipedia.org/wiki/Kernel_same-page_merging
The last was verified on RDO Mitaka. Newton seems to have issues with HA overcloud deployments at least at the time of writing. See https://bugs.launchpad.net/tripleo #1585275, #1629366.
What is sshuttle? It’s a Python app that uses SSH to create a quick and dirty VPN between your Linux, BSD, or Mac OS X machine and a remote system that has SSH access and Python. Been licensed under the GPLv2, sshuttle is a transparent proxy server that lets users fake a VPN with minimal hassle.
***************************************************************************
First install sshutle on Fedora 24 :-
$ dnf -y install sshuttle
Then switch to VIRTHOST an set up standard Linux Bridge
***************************************************************************
# cat ifcfg-br0
DEVICE=br0
TYPE=Bridge
BOOTPROTO=static
DNS1=192.168.1.1
DNS2=83.221.202.254
GATEWAY=192.168.1.1
IPADDR=192.168.1.57
NETMASK=255.255.255.0
ONBOOT=yes
# cat ifcfg-enp3s0
DEVICE=enp3s0
HWADDR=78:24:af:43:1b:53
ONBOOT=yes
TYPE=Ethernet
IPV6INIT=no
USERCTL=no
BRIDGE=br0
***************************
Then run script
***************************
#!/bin/bash -x
chkconfig network on
systemctl stop NetworkManager
systemctl disable NetworkManager
service network restart
Switch to VIRTHOST and follow http://lxer.com/module/newswire/view/234346/index.html until instack VM will be up and running , then shutdown "instack VM" and add third VNIC to this VM and second VNIC to each one baremetal_(X) VMs created by instack-virt-setup run :-
On instack VM create /etc/sysconfig/network-interfaces/ifcfg-eth2 file configured
BOOTPROTO=dhcp && sudo ifup eth2 .
[stack@instack ~]$ sudo su -
Last login: Mon Oct 3 12:32:04 UTC 2016 from 192.168.1.4 on pts/2
[root@instack ~]# cat /etc/sysconfig/network-scripts/ifcfg-eth2
TYPE=Ethernet
BOOTPROTO=dhcp
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
NAME=eth2
DEVICE=eth2
ONBOOT=yes
PREFIX=24
GATEWAY=192.168.1.1
DNS1=83.221.202.254
IPV6_PEERDNS=yes
IPV6_PEERROUTES=yes
IPV6_PRIVACY=no
**********************************************************************************
Issue `ifconfig` and make sure eth2 obtained IP via your office router usually
192.168.1.1. Thus "instack VM" appears to belong mentioned network and would serve as ssh tunnel for sshuttle supposed to provide access to external
network 10.0.0.0/24 which would be created in TripleO Master Branch overcloud
after completion of deployment procedure.
**********************************************************************************
[root@instack ~]# ifconfig
br-ctlplane: flags=4163 mtu 1500
inet 192.0.2.1 netmask 255.255.255.0 broadcast 192.0.2.255
inet6 fe80::222:cdff:fe52:11cf prefixlen 64 scopeid 0x20
ether 00:22:cd:52:11:cf txqueuelen 0 (Ethernet)
RX packets 3203772 bytes 242696157 (231.4 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4663339 bytes 20369572127 (18.9 GiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163 mtu 1500
inet 192.168.122.23 netmask 255.255.255.0 broadcast 192.168.122.255
inet6 fe80::5054:ff:fec7:6356 prefixlen 64 scopeid 0x20
ether 52:54:00:c7:63:56 txqueuelen 1000 (Ethernet)
RX packets 50868 bytes 5455013 (5.2 MiB)
RX errors 0 dropped 2 overruns 0 frame 0
TX packets 44668 bytes 10199981 (9.7 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth1: flags=4163 mtu 1500
inet6 fe80::222:cdff:fe52:11cf prefixlen 64 scopeid 0x20
ether 00:22:cd:52:11:cf txqueuelen 1000 (Ethernet)
RX packets 3218015 bytes 439876673 (419.4 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4672723 bytes 20370569657 (18.9 GiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth2: flags=4163 mtu 1500
inet 192.168.1.14 netmask 255.255.255.0 broadcast 192.168.1.255
inet6 fe80::5054:ff:fe90:4024 prefixlen 64 scopeid 0x20
ether 52:54:00:90:40:24 txqueuelen 1000 (Ethernet)
RX packets 1696493 bytes 2312670704 (2.1 GiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 927189 bytes 266047551 (253.7 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73 mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10
loop txqueuelen 0 (Local Loopback)
RX packets 2468459 bytes 13170730356 (12.2 GiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2468459 bytes 13170730356 (12.2 GiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
vlan10: flags=4163 mtu 1500
inet 10.0.0.1 netmask 255.255.255.0 broadcast 10.0.0.255
inet6 fe80::48c5:c0ff:feff:3d00 prefixlen 64 scopeid 0x20
ether 4a:c5:c0:ff:3d:00 txqueuelen 0 (Ethernet)
RX packets 14440 bytes 196996148 (187.8 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 9337 bytes 947132 (924.9 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Thus eth2 on "instack VM" obtained IP address belongs to office network ( 192.168.1.0/24 ) say 192.168.1.14. Switch back F24 remote WKS and issue as user "john"
[john@fedora24wks]$ export VIRTHOST=192.168.1.14
[john@fedora24wks]$ ssh-copy-id root@$VIRTHOST
[john@fedora24wks]$ ssh root@$VIRTHOST uname -a <== no prompt
Login to instack VM from WKS as root && su - stack && source stackrc
Switch back to instructions from http://lxer.com/module/newswire/view/234346
and proceed with build Tripleo Master Branch undercloud/overcloud.
When done open another terminal session on WKS and issue in this session
[jon@fedora24wks ~]$ export VIRTHOST=192.168.1.14
[jon@fedora24wks ~]$ sshuttle -r root@$VIRTHOST -v 10.0.0.0/24
Due to instack VM is trusting via ssh F24 WKS you won't be prompted to
connection to VIRTHOST and following output will appear in terminal session
Starting sshuttle proxy.
firewall manager: Starting firewall with Python version 3.5.1
firewall manager: ready method name nat.
IPv6 enabled: False
UDP enabled: False
DNS enabled: False
TCP redirector listening on ('127.0.0.1', 12300).
Starting client with Python version 3.5.1
c : connecting to server...
Starting server with Python version 2.7.5
s: latency control setting = True
s: available routes:
s: 2/10.0.0.0/24
s: 2/192.0.2.0/24
s: 2/192.168.1.0/24
s: 2/192.168.122.0/24
c : Connected.
firewall manager: setting up.
>> iptables -t nat -N sshuttle-12300
>> iptables -t nat -F sshuttle-12300
>> iptables -t nat -I OUTPUT 1 -j sshuttle-12300
>> iptables -t nat -I PREROUTING 1 -j sshuttle-12300
>> iptables -t nat -A sshuttle-12300 -j RETURN --dest 127.0.0.1/32 -p tcp
>> iptables -t nat -A sshuttle-12300 -j REDIRECT --dest 10.0.0.0/24 -p tcp --to-ports 12300 -m ttl ! --ttl 42
c : Accept TCP: 192.168.1.4:36580 -> 10.0.0.8:80.
c : Accept TCP: 192.168.1.4:36582 -> 10.0.0.8:80.
c : Accept TCP: 192.168.1.4:36584 -> 10.0.0.8:80.
c : Accept TCP: 192.168.1.4:36586 -> 10.0.0.8:80.
c : Accept TCP: 192.168.1.4:36588 -> 10.0.0.8:80.
c : Accept TCP: 192.168.1.4:36590 -> 10.0.0.8:80.
Open SSH window to instak VM
# su - stack
# source stackrc
Reports above instructs you to launch browser ( on F24 WKS ) to
http://10.0.0.8/dashboard/ . Login password for "admin" is in "overcloudrc" file
generated under ~stack/ folder on "instack VM"
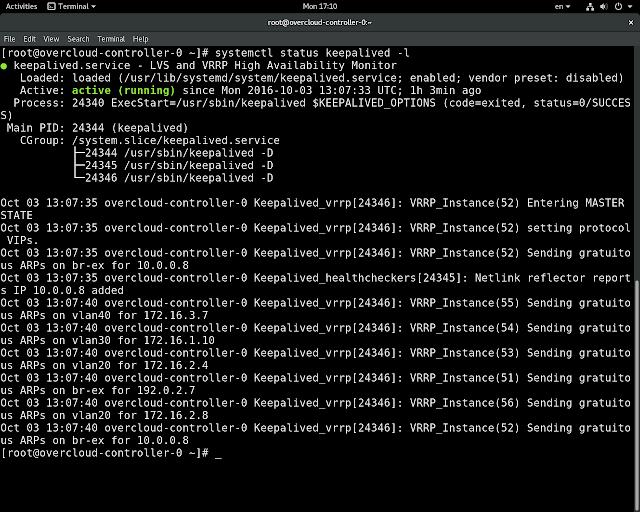
Login to overcloud controller and up on restarting keepalived daemon you are going to get :-
Create VM via nova/neutron CLI sourcing overcloudrc on Controller and make
sure that remote sshuttle connection to "instack VM" via http://10.0.0.8/dashboard will provide you option to manage vms running on overcloud compute
nodes . Also ctlplane (192.0.2.0/24) defined as public network might serve
for outbound Internet connectivity for those vms
ssh (trusted) connection . This setup works much more stable then configuring
FoxyProxy on VIRTHOST running "instack" ( actually undercloud VM) hosting
heat stack "overcloud" and several overcloud Controllers and Compute VMs
Instack-virt-setup deployments don't provide ( vs QuickStart ) ksmd daemon
sharing pages between overcloud VMs ( and supporting copy-on-write feature)
what results significantly more memory utilization on VIRTHOST and require
better CPUs and 48 GB RAM for testing HA overcloud deployments.
Regarding KSM see https://en.wikipedia.org/wiki/Kernel_same-page_merging
The last was verified on RDO Mitaka. Newton seems to have issues with HA overcloud deployments at least at the time of writing. See https://bugs.launchpad.net/tripleo #1585275, #1629366.
What is sshuttle? It’s a Python app that uses SSH to create a quick and dirty VPN between your Linux, BSD, or Mac OS X machine and a remote system that has SSH access and Python. Been licensed under the GPLv2, sshuttle is a transparent proxy server that lets users fake a VPN with minimal hassle.
***************************************************************************
First install sshutle on Fedora 24 :-
$ dnf -y install sshuttle
Then switch to VIRTHOST an set up standard Linux Bridge
***************************************************************************
# cat ifcfg-br0
DEVICE=br0
TYPE=Bridge
BOOTPROTO=static
DNS1=192.168.1.1
DNS2=83.221.202.254
GATEWAY=192.168.1.1
IPADDR=192.168.1.57
NETMASK=255.255.255.0
ONBOOT=yes
# cat ifcfg-enp3s0
DEVICE=enp3s0
HWADDR=78:24:af:43:1b:53
ONBOOT=yes
TYPE=Ethernet
IPV6INIT=no
USERCTL=no
BRIDGE=br0
***************************
Then run script
***************************
#!/bin/bash -x
chkconfig network on
systemctl stop NetworkManager
systemctl disable NetworkManager
service network restart
Switch to VIRTHOST and follow http://lxer.com/module/newswire/view/234346/index.html until instack VM will be up and running , then shutdown "instack VM" and add third VNIC to this VM and second VNIC to each one baremetal_(X) VMs created by instack-virt-setup run :-
On instack VM create /etc/sysconfig/network-interfaces/ifcfg-eth2 file configured
BOOTPROTO=dhcp && sudo ifup eth2 .
[stack@instack ~]$ sudo su -
Last login: Mon Oct 3 12:32:04 UTC 2016 from 192.168.1.4 on pts/2
[root@instack ~]# cat /etc/sysconfig/network-scripts/ifcfg-eth2
TYPE=Ethernet
BOOTPROTO=dhcp
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
NAME=eth2
DEVICE=eth2
ONBOOT=yes
PREFIX=24
GATEWAY=192.168.1.1
DNS1=83.221.202.254
IPV6_PEERDNS=yes
IPV6_PEERROUTES=yes
IPV6_PRIVACY=no
**********************************************************************************
Issue `ifconfig` and make sure eth2 obtained IP via your office router usually
192.168.1.1. Thus "instack VM" appears to belong mentioned network and would serve as ssh tunnel for sshuttle supposed to provide access to external
network 10.0.0.0/24 which would be created in TripleO Master Branch overcloud
after completion of deployment procedure.
**********************************************************************************
[root@instack ~]# ifconfig
br-ctlplane: flags=4163
inet 192.0.2.1 netmask 255.255.255.0 broadcast 192.0.2.255
inet6 fe80::222:cdff:fe52:11cf prefixlen 64 scopeid 0x20
ether 00:22:cd:52:11:cf txqueuelen 0 (Ethernet)
RX packets 3203772 bytes 242696157 (231.4 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4663339 bytes 20369572127 (18.9 GiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163
inet 192.168.122.23 netmask 255.255.255.0 broadcast 192.168.122.255
inet6 fe80::5054:ff:fec7:6356 prefixlen 64 scopeid 0x20
ether 52:54:00:c7:63:56 txqueuelen 1000 (Ethernet)
RX packets 50868 bytes 5455013 (5.2 MiB)
RX errors 0 dropped 2 overruns 0 frame 0
TX packets 44668 bytes 10199981 (9.7 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth1: flags=4163
inet6 fe80::222:cdff:fe52:11cf prefixlen 64 scopeid 0x20
ether 00:22:cd:52:11:cf txqueuelen 1000 (Ethernet)
RX packets 3218015 bytes 439876673 (419.4 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4672723 bytes 20370569657 (18.9 GiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth2: flags=4163
inet 192.168.1.14 netmask 255.255.255.0 broadcast 192.168.1.255
inet6 fe80::5054:ff:fe90:4024 prefixlen 64 scopeid 0x20
ether 52:54:00:90:40:24 txqueuelen 1000 (Ethernet)
RX packets 1696493 bytes 2312670704 (2.1 GiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 927189 bytes 266047551 (253.7 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10
loop txqueuelen 0 (Local Loopback)
RX packets 2468459 bytes 13170730356 (12.2 GiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2468459 bytes 13170730356 (12.2 GiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
vlan10: flags=4163
inet 10.0.0.1 netmask 255.255.255.0 broadcast 10.0.0.255
inet6 fe80::48c5:c0ff:feff:3d00 prefixlen 64 scopeid 0x20
ether 4a:c5:c0:ff:3d:00 txqueuelen 0 (Ethernet)
RX packets 14440 bytes 196996148 (187.8 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 9337 bytes 947132 (924.9 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Thus eth2 on "instack VM" obtained IP address belongs to office network ( 192.168.1.0/24 ) say 192.168.1.14. Switch back F24 remote WKS and issue as user "john"
[john@fedora24wks]$ export VIRTHOST=192.168.1.14
[john@fedora24wks]$ ssh-copy-id root@$VIRTHOST
[john@fedora24wks]$ ssh root@$VIRTHOST uname -a <== no prompt
Login to instack VM from WKS as root && su - stack && source stackrc
Switch back to instructions from http://lxer.com/module/newswire/view/234346
and proceed with build Tripleo Master Branch undercloud/overcloud.
When done open another terminal session on WKS and issue in this session
[jon@fedora24wks ~]$ export VIRTHOST=192.168.1.14
[jon@fedora24wks ~]$ sshuttle -r root@$VIRTHOST -v 10.0.0.0/24
Due to instack VM is trusting via ssh F24 WKS you won't be prompted to
connection to VIRTHOST and following output will appear in terminal session
Starting sshuttle proxy.
firewall manager: Starting firewall with Python version 3.5.1
firewall manager: ready method name nat.
IPv6 enabled: False
UDP enabled: False
DNS enabled: False
TCP redirector listening on ('127.0.0.1', 12300).
Starting client with Python version 3.5.1
c : connecting to server...
Starting server with Python version 2.7.5
s: latency control setting = True
s: available routes:
s: 2/10.0.0.0/24
s: 2/192.0.2.0/24
s: 2/192.168.1.0/24
s: 2/192.168.122.0/24
c : Connected.
firewall manager: setting up.
>> iptables -t nat -N sshuttle-12300
>> iptables -t nat -F sshuttle-12300
>> iptables -t nat -I OUTPUT 1 -j sshuttle-12300
>> iptables -t nat -I PREROUTING 1 -j sshuttle-12300
>> iptables -t nat -A sshuttle-12300 -j RETURN --dest 127.0.0.1/32 -p tcp
>> iptables -t nat -A sshuttle-12300 -j REDIRECT --dest 10.0.0.0/24 -p tcp --to-ports 12300 -m ttl ! --ttl 42
c : Accept TCP: 192.168.1.4:36580 -> 10.0.0.8:80.
c : Accept TCP: 192.168.1.4:36582 -> 10.0.0.8:80.
c : Accept TCP: 192.168.1.4:36584 -> 10.0.0.8:80.
c : Accept TCP: 192.168.1.4:36586 -> 10.0.0.8:80.
c : Accept TCP: 192.168.1.4:36588 -> 10.0.0.8:80.
c : Accept TCP: 192.168.1.4:36590 -> 10.0.0.8:80.
Open SSH window to instak VM
# su - stack
# source stackrc
Reports above instructs you to launch browser ( on F24 WKS ) to
http://10.0.0.8/dashboard/ . Login password for "admin" is in "overcloudrc" file
generated under ~stack/ folder on "instack VM"
Login to overcloud controller and up on restarting keepalived daemon you are going to get :-
Create VM via nova/neutron CLI sourcing overcloudrc on Controller and make
sure that remote sshuttle connection to "instack VM" via http://10.0.0.8/dashboard will provide you option to manage vms running on overcloud compute
nodes . Also ctlplane (192.0.2.0/24) defined as public network might serve
for outbound Internet connectivity for those vms